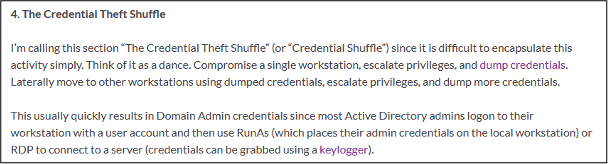
The following is an example of an overly pragmatic implementation, which was more common in the past in enterprises but does not address many risks:
All administrators are given, in addition to the regular user account, an additional administrator account that is used from the regular notebook to administer all tiers (including domain administrator accounts).
These are the penetration tests that are easy and in which it is often possible to compromise the domain the first time before lunch.
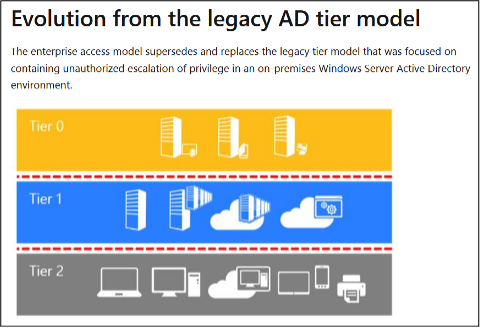
Classification of systems in (three) tiers
There is also a lot to consider when classifying systems into the individual tiers to ensure that the new construct provides the desired security benefit. The basic rule is:
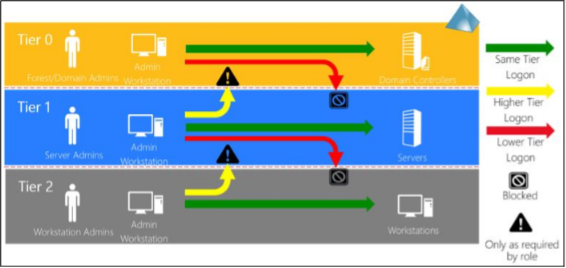
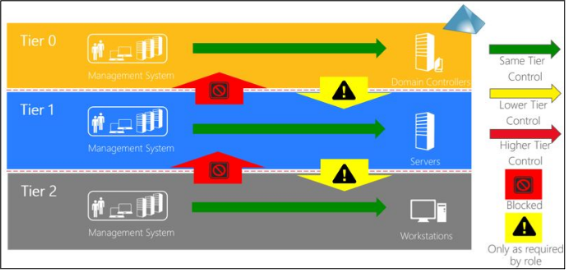
A system that has control over another system must be at the same level or higher.
The reverse numerical order must be observed: Tier 0 is “highest tier” despite lowest number.
It is recommended to take the top-down approach to classification and start with Tier 0. The systems typically to be classified have already been listed at the beginning. On closer inspection, the classification is only obvious and indisputable for a few of these systems.
Thus, the following systems appear to be Tier 0:
- Domain controllers
- ADFS servers
- Entra ID Connect server
- PKI
Obviously, application servers belong to Tier 1, while clients obviously belong to Tier 2.
With the other central systems in the list, it becomes more difficult, and various questions arise:
- Virtualization hardware/software
- Are Tier 0 systems being virtualized here
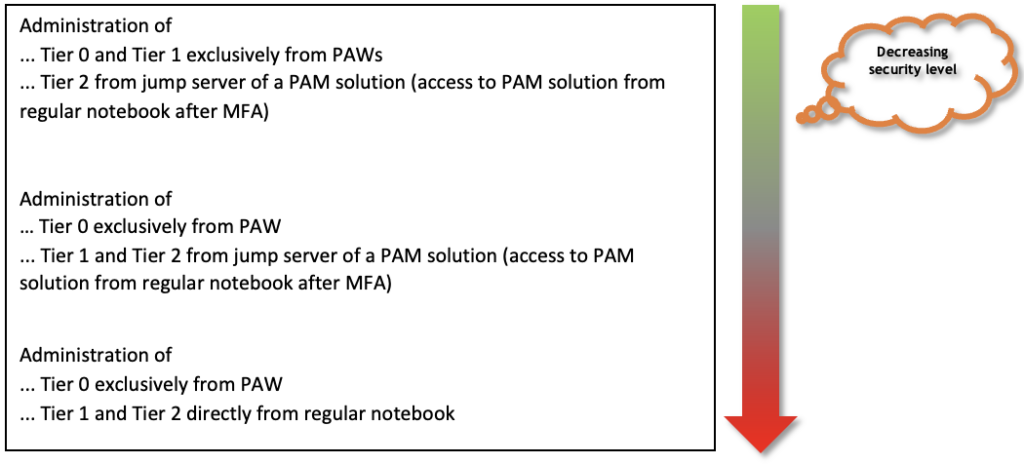
- Privileged access workstations
- Are multiple tiers managed by one category of PAWs or are there separate PAWs by tier?
- Central password management
- The passwords of which tiers are stored here and who needs access?
- Monitoring system (e.g. SCOM)
- Are Tier 0 systems also monitored and is control over these systems possible from the monitoring system?
- Software distribution (e.g. SCCM, WSUS)
- Are software or Windows updates also distributed to Tier 0 systems?
- Backup system/storage
- Are Tier 0 systems or their data stored here?
- Antivirus solution, EDR
- Is administrative control over Tier 0 systems possible via this?
When a company first thinks about this topic, it typically comes to the conclusion very quickly that many central systems must be counted as Tier 0. This shows that until now, many administrators have been unknowingly overprivileged. An example frequently encountered at companies illustrates this:
A company operates a central WSUS server that provides updates for all clients, servers and domain controllers. The release of updates and the administration of WSUS are performed by the regular help desk/server administrators. An attacker only needs to compromise one of these administrators to be able to inject a malicious WSUS update to compromise a domain controller. Compromising such an administrator (Tier 1 or 2) is often significantly easier than compromising a domain administrator (Tier 0) because these user accounts are used on a variety of easily compromised systems (such as regular clients or servers).
To create a malicious WSUS update, an attacker can use ready-made open-source tools such as SharpWSUS (https://github.com/nettitude/SharpWSUS), which are freely available on the Internet. With a few command line calls, the update is created, approved and the attacker only has to wait for the update process. However, the payload must be signed by Microsoft. But this is not a problem either, because programs like psexec.exe, msiexec.exe or msbuild.exe from Microsoft itself can be used for this purpose.
Comparable attack paths can often be developed for other systems on the aforementioned list with little effort.
There are three ways to solve this problem in the context of the tiering model:
Possibility 1
The central system gets the highest classification of systems it can control (e.g. Tier 0). All administrators who need access are given a Tier 0 admin account and use it to work according to Tier 0 standards (e.g. from PAWs). This is a secure solution because strict separation of administration of systems by tiers is implemented and administrative access to the central system over the network can be easily restricted.
The disadvantage is that the number of admin accounts belonging to Tier 0 can become very large, which may not be desirable in itself and can be expensive (e.g. because of the acquisition of many PAWs).
Possibility 2
Multiple instances of the central system are implemented, separated by tiers, e.g., a separate software administration per tier. This is also a secure solution, as there is again strict separation of the central systems by tiers and network access to the remote management interfaces can be easily restricted via the network.
But here, too, the disadvantage is that this solution can quickly become expensive, as additional hardware and software may have to be purchased and the administrative effort increases.
Possibility 3
This solution tries to find a compromise between security requirements and additional costs. Also, it is only suitable for systems that have extensive RBAC (role-based access control). It must therefore be possible to regulate the assignment of permissions within the central system on a granular basis.
Consideration can then be given to classifying the central system as a Tier 0 system but authorizing Tier 1 and Tier 2 admin accounts for the systems at their respective tiers via permission assignment.
A classic example of this is the assignment of permissions within VMware’s vCenter for the VMs of different tiers for the various tier users. Scrupulous care must be taken to ensure that, for example, no Tier 1 or Tier 2 admin accounts are given rights on Tier 0 systems. The advantages here are that there are fewer costs for hardware/software licenses and for the increased administrative overhead than with the previously mentioned options.
However, one of the big disadvantages of this option is that, for example, vulnerabilities in the system itself or in RBAC can endanger the systems of a higher tier starting from lower tiers or tier users. There have been vulnerabilities of this type in various solutions in the past, allowing exactly this attack.
Furthermore, the system is more difficult to isolate on the network side, since a larger number of lower-tier administrators need access to the remote management interfaces.
In addition, this is not a universal solution, as not all systems offer the possibility of granular rights restriction.
On the subject of terminal servers, it should be noted that even though systems in the terminal server category have the word “server” in their name, it is still imperative that they be counted as Tier 2 and treated as clients when used by regular users.
Typically, a large number of users have access to the servers, many different programs are often installed on the terminal servers, and the terminal servers are also often in use for a long time, so many vulnerabilities can accumulate over time. An attacker who manages to gain local administrative rights on a terminal server can compromise a large number of logged-in users at once. Consequently, administrators from higher Tier 1 and, of course, from Tier 0 should never log in here. To the author, privilege escalation vulnerabilities in typical terminal server or Citrix environments have served countless times as starting points for attack paths to compromise the domain.
Note: Parts of this blog post series have already been published in the German IT magazine called “iX” https://www.heise.de/ix